SBounty - Project
Sbounty is a script that leverages a combination of tools developed in bash and golang to create pipelines aimed at detecting vulnerabilities in web applications.
This tool analyzes the routes obtained from a given URL in order to identify potential vulnerabilities, including XSS, SQLi, CORS, LFI, SSTI, Open Redirect, and SSRF.
Link to the Github repository
Installation
Clone the repository and make the script executable:
git clone https://github.com/shockz-offsec/SBounty.git
cd SBounty
chmod +x sbounty.sh
Tools Auto-Installed
- Golang
- Gf-Patterns
- SQLMap
- waybackurls
- gf
- qsreplace
- rush
- freq
- subjack
- httpx
- gauplus
- uro
Usage
Usage: ./sbounty.sh [-s subdomain] [-t]
TARGET OPTIONS
-s subdomain Target subdomain
MODE OPTIONS
-t Subdomain Takeover - Perform a subdomain takeover check
-h Help - Show this help
USAGE EXAMPLES
./sbounty.sh -s tesla.com
./sbounty.sh -s www.tesla.com
./sbounty.sh -s https://www.tesla.com
./sbounty.sh -s 127.0.0.1:8080
Subdomain Takeover check:
./sbounty.sh -s www.tesla.com -t
On the other hand, the vulnerabilities to be scanned can be enabled or disabled through the configuration file.
In the case of SSRF, it is necessary to provide the URL of a server such as Burp Collaborator or Interactsh to receive the requests.
config.ini
#################################################################
# Sbounty config file #
#################################################################
# General values
xss=false
sqli=false
cors=false
lfi=false
ssti=false
open_redirect=false
# SSRF
ssrf=false
burpcollaborator="" # https://xx.yy.zz
#---#
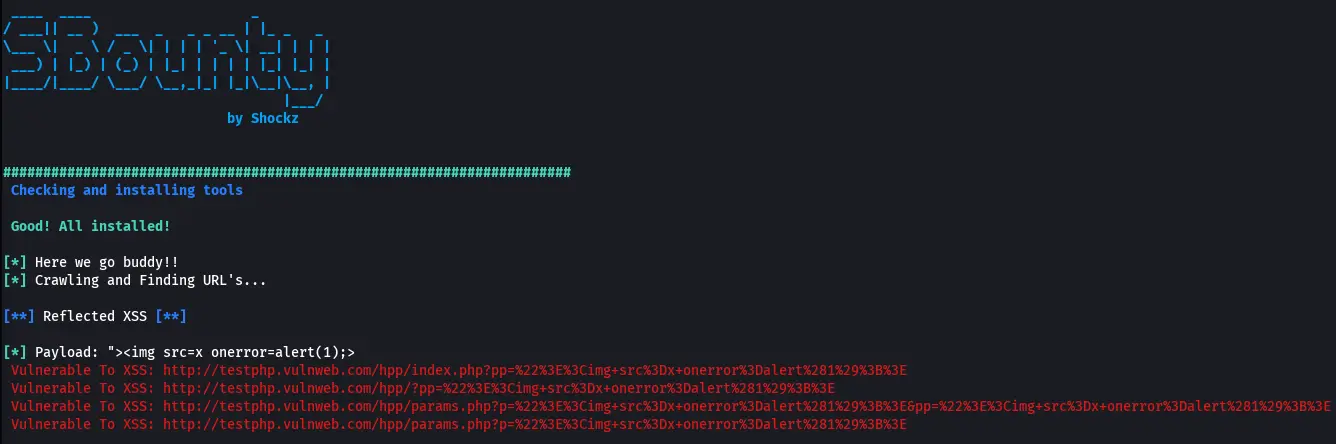
Example
Disclaimer
This tool is designed for legal use only, such as testing and monitoring of systems that you own or have permission to test. Any other use is illegal and at your own risk. The author is not responsible for any damage caused by misuse or illegal use of this tool.
License
This tool is licensed under the GPL-3.0 license.

 Hack The Box
Hack The Box
 Try Hack Me
Try Hack Me